The 2-Minute Rule for How to Spy on Any Mobile Device Using Kali Linux
Installation isn’t the sole trouble you’ll be dodging. Everyone knows that elaborate products tend to existing elaborate support troubles from time to time, and these is often tough to tackle without assistance.
Compared with malicious hackers, ethical hackers hold the authorization and acceptance of your Business which they’re hacking into. Find out how you can build a occupation from screening the security in the network to battle cybercrime and boost information security.
Penetration screening, or pen tests, is one of the most acknowledged programs of ethical hacking. It requires a simulated cyberattack on a procedure, executed beneath managed conditions.
No cost two-day shipping is usually a reliable start, but there’s plenty a lot more to appreciate below. Totaltech membership also incorporates the My Very best Obtain system, which allows you to earn rewards factors on every
Each and every Corporation will need to have a rational security evaluate in place. This might also include cognitive cybersecurity measures adopted by an organization which operates on an incident response program.
Cybersecurity is usually a set of processes, ideal tactics, and technology alternatives that support guard your essential methods and details from unauthorized accessibility. An effective software reduces the risk of small business disruption from an assault.
Netsparker’s special and dead correct Proof-Based Scanning technology does not just report vulnerabilities, Furthermore, it makes a Proof-of-Notion to confirm they aren't Wrong positives. Releasing you from being forced to double Verify the discovered vulnerabilities.
The cybersecurity landscape proceeds to evolve with new threats and alternatives rising, which include:
Ethical hackers have several roles in the Corporation they work for. Thinking about The reality that ethical hacking is adopted by public and private organizations alike, targets may wind up getting assorted, but they may be boiled down to a couple crucial factors –
Hiring administrators choose to see that you're proficient in a variety of functioning units, firewalls, and file techniques. You'll need powerful coding expertise plus a strong foundation in Pc science.
Following the screening period of time, ethical hackers get ready a detailed report that includes added facts on the identified vulnerabilities coupled with ways to patch or mitigate them.
Ethical hacking should be to scan vulnerabilities and to seek out opportunity threats on a computer or network. An ethical hacker finds the weak factors or loopholes in a pc, Internet application or community and experiences them for the Group. So, let’s check out more details on Ethical Hacking move-by-stage. These are definitely different sorts of hackers:
Should you subscribed, you obtain a 7-day absolutely free demo through which you'll be able to cancel at no penalty. Following that, we don’t give refunds, however you can cancel your membership Anytime. See our complete refund policyOpens in a completely new tab
Here are a few tools you must study in order to be an Total Tech efficient and expert ethical hacker. These instruments are market-normal and will almost certainly be Utilized in the business you want to get into. Enable’s evaluate Each individual one of them.
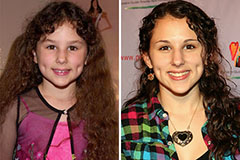 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Shane West Then & Now!
Shane West Then & Now! Soleil Moon Frye Then & Now!
Soleil Moon Frye Then & Now!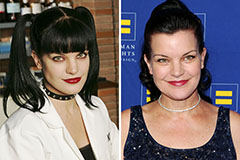 Pauley Perrette Then & Now!
Pauley Perrette Then & Now! Erika Eleniak Then & Now!
Erika Eleniak Then & Now!